Incident Response: Using Process Explorer to look for malware
At The Cyber Security Expert we’re often asked about incident response – what to do when things go wrong, and how to work out if a particular computer is compromised. Obviously we are here to help you if needed, but there is quite a lot you can do yourself (as you will have seen if you read our posts on spotting malicious email, and dealing with suspect files). This post explains how to use a free tool, Process Explorer, to spot malicious software running on a computer.
What is Process Explorer?
Process Explorer is part of the Sysinternals suite (acquired by Microsoft) created by Mark Russinovich. It is like Windows Task Manager but offers many more featrues. It has been a popular tool amongst IT professionals for a very long time. Among its impressive list of features are:
- hierarchical parent relationship between processes
- identify which process has loaded a DLL file or has a file or folder open and locked
- kill or suspend a process tree including any spawned processes
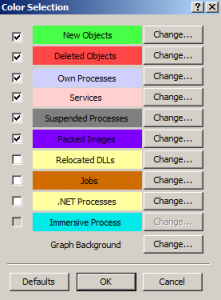
- its colour coded list of processes is a favourite feature of ours and makes for simplified analysis
This level of granularity has helped track down DLL version problems and memory leaks in general application analysis as well as malware analysis. In order to see the most amount of information about each process it is best to run Process Explorer as an Administrator. You can read more about Process Explorer features, and download it, here.
Virustotal again
Since version 16 (~ January 2014) Process Explorer has included integration with Virustotal. Virustotal (a subsidiary of Google) runs multiple (approximately 50) anti-virus engines and brings together all of that knowledge. This means if your anti-virus program does not detect a file as malicious but another provider does you can identify the problem sooner! We’ve spoken about Virustotal previously (in our article here) – it’s an extremely useful website, which will you use a lot if you do much cyber security related work.
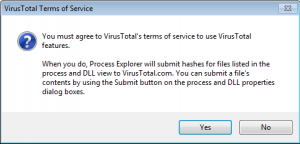
Before you can check or submit a file using Process Explorer you need to opt-in (you only need to do this once).
Once you’ve done this all executables running on your computer will automatically be checked against the list of all files that have previous been submitted to Virustotal, as we demonstrate below. A brief explanation of how this is done would be useful at this point. There is a cryptographic function known as hashing – in essence it is a way of fingerprinting a particular file. A hash should be unique (that’s not quite true in reality, but for practical purposes here we can consider it to be), meaning I can generate a unique, fixed length, fingerprint for any computer file. When a file is uploaded to Virustotal for analysis, Virustotal generates one of these fingerprints. Process Explorer does the same thing for all the executables running on your computer, and then checks these fingerprints against those stored on Virustotal. Any that match must be the fingerprints of matching files. This enables Process Explorer to check your running executables against the huge Virustotal database of malicious software, without having to upload each file for analysis.
Finding malware
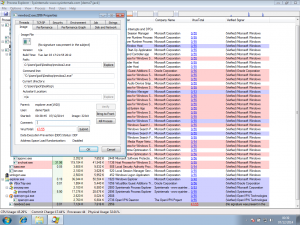
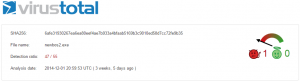
We’re going to infect our demo computer with a piece of malware (malicious software) from the team at Tekdefense. We selected a sample from their malware library, downloaded it to our computer and ran it, infecting the machine. Running Process Explorer shows the following (the malicious process is ‘newbos2.exe’ – click the image to enlarge):
Straight away you can see the executable is malicious. Virustotal shows 47 out of 53 anti-virus vendors have flagged the exe as malicious (the sixth column in the screenshot). This particular malware is used to infect Windows hosts and become part of the Kelihos botnet which has been used in sending spam and in the theft of Bitcoins.
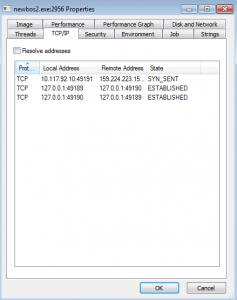
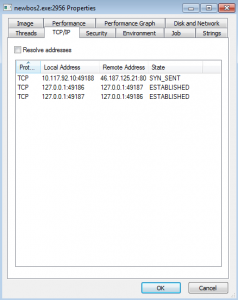
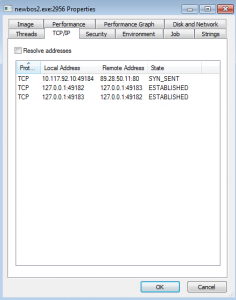
Through the Properties menu in Process Explorer, we can see the malware connecting out to other compromised computers on the internet for further instructions and operations
Approximately 40 connection requests were made in 30 minutes. In our example there were no responses to these connections as this version of the botnet was disrupted by the authorities some time ago.
If you’re worried a PC might be running something malicious, this is a great way to check without having to download a whole range of antivirus products. For security analysts the built-in Virustotal support, including network connection monitoring, can speed up analysing executables in a sandbox environment. This feature is great at spotting known malware. Further, Process Explorer supports submissions to Virustotal. If this option is selected currently unknown executables running on your computer can be submitted to Virustotal for analysis.
This will upload the executable in question to Virustotal, and run it through the range of antivirus products. Even if Virustotal has not seen your particular file before, you will be able to see if any antivirus products flag it as malicious.
What next?
This is a great way to detect malicious software, and to begin your incident response process. We’ll address what you should do when you do find something bad in a future post.
As always, if you have questions please get in touch! Find us on twitter, or use the contact form.
The Cyber Security Expert