GDPR and Security Monitoring
The NCSC, along with the Information Commissioners Office (ICO) have produced some useful guidance on security and GDPR. The approach they use distill nicely into four aims;
- Manage security risk
- Protect personal data against cyber attack
- Detect security events
- Minimise the impact
I will write blogs on all of these points, but today I want to focus on the third one; detect security events.
Let’s start by defining what it is we’re talking about. Security monitoring means watching who is using your systems and accessing your data, and trying to spot suspicious and malicious events. These events can be external hackers trying to break-in and steal your data or hold you to ransom, or people inside your company doing the wrong thing either deliberately or unwittingly. Monitoring is usually achieved through some technical means; collecting and analysing audit data from services or devices, or looking at network traffic. Regardless of the technical way security monitoring is done, at some point there will have to be a person in the loop looking at the output and taking some action.
How to do security monitoring
For a modern organisation there are three main points in your environment that you can effectively conduct security monitoring, and I am listing them in what I think is a reasonable priority order for SMEs in particular (I’ll explain my reasoning below, and of course there are caveats):
- On your cloud providers
- On your endpoint (and by this I mean laptops, desktops etc)
- On your network
Monitoring Cloud Providers
If you are a big user of cloud services, then the place to start your security monitoring is at the services you use. Security monitoring in this context means looking for suspicious things including;
- Suspicious logins e.g. Why is someone logging in from China when we have no staff there? Should someone be logging in from a free VPN service provider? How is John logged in from Utah and Croydon at the same time?
- Failed logins e.g. did Susanne really forget her password 60 times?
- Potentially suspicious or harmful behaviour e.g. inappropriate information sharing with a third party, forwarding of email to a personal address.
Most cloud service providers do make this kind of data accessible (typically called audit or security data), and you can usually find it somewhere if you log in as an administrator. Dropbox for instance as a search tool you can use to see what users have been doing, and allows you to generate reports which it emails to you. However, this approach doesn’t scale well – if you have anything above even a small number of users, using even a small number of different services they will generate lots of audit events. Interpreting all that data is not easy and even worse you might only discover a breach sometime after the event.
Realtime monitoring with some sort of alerting is therefore desirable, and you have two options;
- You can do it yourself if you have the internal capability
- You can pay someone else to do it for you
If you are an Office 365 user I have some good news – you can purchase (priced per user) a monitoring capability which alerts you to the sorts of events I’ve outlined above. You will still need to manage the service, and review and act on the alerts it sends you but it is easy to set up and use. The MS service even allows you to connect some other third party services, so you can review those events too.
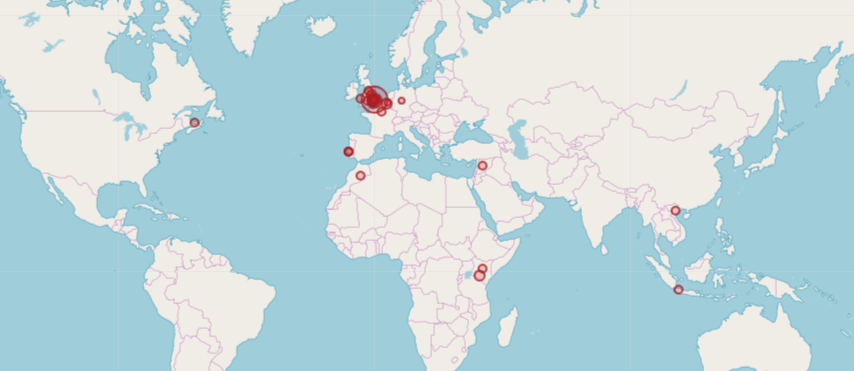
If you don’t have the in-house capability then going to a security service provider is the way forward. Typically they can ingest events from a variety of cloud services, and produce reporting and alerts on the sorts of criteria we have discussed. We provide this kind of service, giving our clients visibility of where from and when their cloud hosted data and applications are being accessed (the banner picture at the top a screen shot of geolocated O365 logins).
Monitoring Endpoints
Typically endpoint monitoring involves installing a small piece of software on every computer which talks back to a central command centre, and gives you visibility of, and in some cases the ability to manage, what is happening on the device. There is a big range of commercial products in this space (both delivered as a service and just as a product), and plenty of them are very good. The downside is none of them is very cheap. And again, there are free products you can use (have a look at Sysmon, which is a Microsoft tool), which deliver much of the functionality.
The approach you chose is going to depend on your organisation; you need to consider what internal capability you have to implement a solution and do the actual monitoring yourself vs getting someone else to do it for you. Also, whatever solution you chose you will still have gaps – if you allow staff to use their own devices you won’t get visibility of those (most people are rightly not keen on software that can monitor everything they do being installed on their personal devices). Likewise, you might not be able to cover the entirety of the estate you own – Windows is easy, but tablets, company mobiles, and even some non-Windows operating systems are likely to be challenging.
Monitoring the Network
Now historically I’d have said the network was the most important element of a security monitoring posture, and would have recommended some form of NIDs (network intrusion detection system). NIDs however does not deliver all it once did in the modern working environment, largely due to more mobile workforces, BYOD (bring your own device) and cloud services. A NIDs implementation requires you install some form of sensor on your network to analyse network traffic, and it will give you great visibility of what is happening.
However if your employees are off traveling, or working from home, or otherwise not in the office, and they are connecting to Office 365 or Dropbox, or Gmail or any of the myriad other cloud providers, their network traffic is never actually coming anywhere near your physical network. Indeed, plenty of organisations don’t even have a physical network anymore.
I’m not saying NIDs are dead – we work with clients frequently on NIDs projects. If you have a physical network, and still host services internally, or have staff who all come to a physical office, then it is still worth doing. A great solution (even for enterprises) is Security Onion (https://securityonion.net/) – free, great community support and does everything you could want. Plus, you can pay for support if you want it.
I hope the above has provided a useful overview of security monitoring, and given you some idea of what approach is best for you and your organisation. We provide a cloud monitoring service, so get in touch if you’d like to know more about it. We also work with organisations to develop and implement security monitoring strategies, which can include building in-house capability or working with clients to find the right outsourcing solution for them. It’s an area in which we have a lots of experience, so do get in touch if that’s something you’d like help with. And of course feel free to hit us up with any questions you might have more generally. We are always happy to help.
Contact us on twitter or use our contact form.
Thanks for reading
Rob
