There’s something about Alia
Today I haven’t been asked anything. Instead I’m going to ramble on about trust, and social media and what all that means for us in this modern era.
Lets start at the beginning
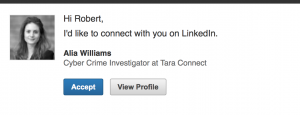
In the beginning, there was the word. And the word was tea. Whilst drinking my tea this morning, slowly coming round, I did as I usually do, which is to pretend I’m working by reading online comic strips and checking Twitter. I do also check email though, and this morning I had an interesting one. It looked like this:
Hello, I thought, sitting up a bit straighter and brushing the toast crumbs from my beard. This is interesting. Lets connect! And my pointer hovered over that ‘Accept’ button. But you don’t get to be The Cyber Security Expert if you trust everything you see online. I decided to check out Alia’s profile.
Background Cheques
This is Alia’s experience:
Looks reasonable. Ok, I don’t know what TECHINT or CYBERINT are, but it’s pretty much par for the course for anyone with ‘cyber’ in the job title these days. But still, I’m a cynic. I’ve never heard of Tara Connect. I don’t expect you have either. There appears to be someone on LinkedIn called Tara Connect (which may well be a real name – the world is a big place) but I can’t find anyone else who works for a company with that name. At all. On the whole of LinkedIn. And it has apparently got 600 employees. Maybe they have really good OPSEC.
Equally, unless my Google fu is really off, there is no website for a company called Tara Connect. There is a Tara Security but they are a London based burglar alarm company. I doubt they do much TECHINT.
Lets get social
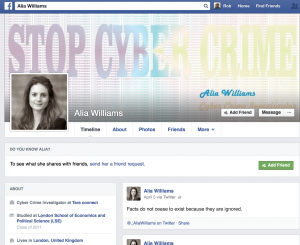
Alia has links to her Twitter and Facebook profiles. How helpful. But they are, how can I put this, flimsy looking:
She has three whole friends. Now I’m no expert (except in cyber security) but that doesn’t look like the Facebook page of a recent graduate. It does look like some flashback to Geocities, albeit with a positive social message.
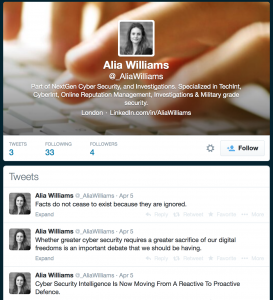
What about Twitter?
Three whole tweets.
Lets get connected
By now my cybersense was definitely tingling. Alia does’t seem terribly well fleshed out. But, she does have 212 connections on LinkedIn (thats gone up since my initial look). She also has three connections in common with me. I got in touch with one of them and asked if he knew Alia. He does not. He did think the profile looked a bit sparse, but assumed it was just a graduate starting out, and anyway she was well connected with other people he know. So he clicked the ‘Accept’ button.
I think at this point we can safely conclude Alia is not a real person. Her profile includes her email address – I have sent an email, but not received a reply.
The serious bit
There are some serious points here. I have no idea who is behind this profile, or why, but someone is clearly trying to build a big network of LinkedIn connections. This has been done before just to illustrate the point by security researchers, but equally social media is often used to target people for malicious reasons.
Social engineering is the art of duping people into doing what you want them to do. A lot has been written about it (Kevin Mitnick is an expert in this field – his book is worth a read), but it all ultimately boils down to persuasion. There are a few of the core concepts at play here. Firstly, and its stating the obvious, but we are more likely to respond positively to people we are attracted to. Obviously there is more to ‘attraction’ and ‘liking’ than the way someone looks, but for social media, where there is no dialogue, its a good hook. People seeing Alia’s photo are quite likely to respond positively and apply less scrutiny than they would to a picture of some crouchy cynic with crumbs in his beard.
Secondly, you are much more likely to go along with a suggestion from someone if you have done something for them in the past. If you’ve helped me out before, even in a innocuous way, you are more likely to respond positively when I ask you for the company secrets (ok, you need to build up to that, but this technique can be used to draw people into eventually doing things they would have resisted had you asked up front). If you’re connected to Alia, and have been for sometime, the day you get an LinkedIn message from her asking a question you will treat it much less cautiously than you would had the contact come from someone completely unknown. Again, this is a common technique for getting people to give up sensitive information.
On Trust
Finally, we come to trust. The guy I spoke to placed a degree of trust in Alia’s profile because she was connected to people he knew. Clicking that ‘Accept’ button is not a passive act. You are making a positive decision about trust, which may come back to bite you. Equally you are potentially providing someone nefarious with implied trust in you. Oh, Alia is connected to X, she must be ok.
So be cynical! Verify before accepting requests like this. You are a primitive herd beast, poorly equipped to deal with the modern world. You are easily manipulated by people who don’t play by the rules, and that intuition that serves you well in the real world can let you down badly online.
If I get a reply to my email, I’ll update this post. Equally if you know Alia, and I’ve made a terrible mistake, let me know (and I’ll take back the criticism of the Facebook page).
As always, thanks for reading.
Find us on twitter, or use the contact form.
The Cyber Security Expert