From Russia with love: phishing, hacking and intelligence
I’m going to deviate from the usual ‘ask the expert’ today and talk instead about something I very much enjoy, which is digging around in data, and at the same time highlight the threat from what are apparently Russian state backed hackers. Sounds very Cold War right? Shake that martini and lets go!
APT28
Regular readers will know here at The Cyber Security Expert we’re not a fan of jargon, and one of my least liked acronyms is ‘APT’. You can read what it means here. I’m going to let it slide today, as I am clearly in the minority.
APT28 are a group of hackers assessed by FireEye to be Russian state sponsored. You can download the report and read their rationale here – it’s worth doing. I’m not going to into any depth on the validity of their assessment, beyond to say it looks fairly sensible to me, and the UK’s Intelligence and Security Committee (ISC) who provide oversight of the UK intelligence agencies have been warning about the threat from Russian and Chinese state backed hackers (cyber espionage in other words) since their 2008 – 2009 annual review, which you can you download and peruse at your leisure here. It’s actually worth doing, they contain a surprising amount of interesting information, and show how the priorities of, and challenges for, the UK agencies have changed over the years (the reports go back as far as 1995).
FireEye are not the only people getting in on the act – iSight released a report about a group they called Sandworm (due to all the Dune references – kudos for that one Russian cyber spooks). Also a good report and worth a read, and is notable as subsequent investigations by security researchers uncovered compromises of industrial control networks by this group. In other words hacking that could potentially be physically disruptive. Finally PWC pushed a report about a group referred to as ‘Sofacy” which has technical links to the APT28 group.
So the Russians hack to gain intelligence and lots of people have pushed out reports on it. What does this mean to you dear reader?
A couple of things. Firstly you might have been a target for Russian espionage yourself. Those reports, and some further info I’m about divulge might help you check that, and secondly if you get any sort of cyber security marketing at all you’ll probably know you should have an intelligence lead approach to dealing with threat. Lots of people say that, few can say what it means. So we’re going to have a dig into one way you might use the information in these reports to generate your own intelligence, and potentially prevent future compromises of your organisation.
An intelligent approach
So lets begin. Intelligence is one of those words which when used in it’s spooky context causes a lot of people to nod intelligently in the hope of looking like they agree, and could add more but, you know, they can’t talk about it. At least thats what I do. But actually for practical purposes it can just mean doing a bit of googling about something and seeing what you can turn up. Taking one bit of information, and finding more bits of information in other words.
The APT28 report (thats the one I’m going to focus on) contains details of a number of domains (a domain is something like example.com, or my_russian_hacking_site.org) used by the threat actors. Domains have to be registered – you can’t just make them up and start using them, and when you register a domain with a registrar (there are companies responsible for this sort of thing) you need to provide some contact details.
These are the domains in APT28 report:
standartnevvs[.]com
novinitie[.]com, n0vinite[.]com
qov[.]hu[.]com
q0v[.]pl, mail[.]q0v[.]pl
poczta.mon[.]q0v[.]pl
nato.nshq[.]in
natoexhibitionff14[.]com
login-osce[.]org
Those are all designed to look very like real domains, and the [] are used to prevent pdf readers, or whatever else you may use, automatically recognising them as links. First rule of any kind of investigation or incident response is not to get compromised yourself. Those domains are all used by alleged Russian spooks. Do not visit them, and do not store them in a way which means you may accidentally click on one.
Domain Registrations
For each of those domains the Russian hackers would have had to provide some contact details. Names, phone numbers and addresses can be made up but you do need to provide a valid email address that you can access. Registering one with a webmail provider is not difficult, but it is an extra hoop to jump through. And therein lies the opportunity for us, as defenders. People are lazy. I know I am. You’ve registered a fake webmail account and you’re setting up your domains for use in your nefarious espionage. It’s hassle. Why not save some time and use the same email address to register a bunch of domains?
Now, the reason you don’t do that is that if one of those domains gets blown and ends up in a report like this, people can search on the email address you used for that domain and find all the other malicious domains you registered. And there goes your covert infrastructure, which is a pain when that nice Mr Putin specifically wanted those documents from NATO for the weekend. Luckily for us, as I mentioned, people are lazy.
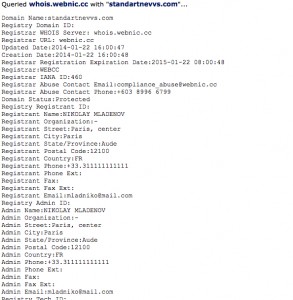
I went through each of the domains above, checked the registration details, and then searched using those registration details to see what I could find. Checking domain registrations is easy – there are lots of websites that will do it for you. I like, and use a lot, CentralOps. This is what the CentralOps output looks like for the first of those domains, standartnevvs[.]com:
You can see this was registered by someone using the name ‘NIKOLAY MLADENOV’ and the email address ‘mladniko@mail.com’.
Searching on that email does not reveal much of additional interest – that email address was also used to register the next two domains listed above (novinitie[.]com, n0vinite[.]com). So lets move onto something interesting.
qov[.]hu[.]com was registered using ‘nikodima@mail.com’. This email is associated with domains not in the report:
livemicrosoft[.]net
sofexjordanx[.]com
yovtube[.]co
Digging into those domains actually led me to the PWC report, so someone else beat me to it, but you can see how you are starting to get extra useful information. If you block those domains on your web proxy, or add them to your monitoring tools, you are one step ahead of the attackers. Instead of responding you’re being proactive. And that feels nice.
Phishing
The next domain I found interesting is nato.nshq[.]in. This was registered using the email ‘aksnes.thomas@yahoo.com’. Googling this shows it was linked to phishing attacks aimed at users of Gmail earlier in the year. More detail here, but in essence targets received a spoofed email claiming to have blocked a possibly malicious login attempt to their Gmail account. The email also contain what appears to be a link to Gmail to enable the target to login into their Gmail account and check everything is ok. In fact, it linked to a spoof site which had been registered using, tada!, ‘aksnes.thomas@yahoo.com’.
That means people receiving what looked like a reasonably well put together, but run of the mill, phishing email may actually have been a target of Russian state espionage. The source code of the phishing page contained yet another email address: valsowrom@gmail.com. I could turn up nothing useful with this one – the blog post I linked to above speculates it may be the email address of the attacker, but it seems more likely to be another address created specifically for these malicious purposes.
NATO
The last domain of interest was natoexhibitionff14[.]com. The was registered using ‘cowrob@mail.com’. This turned up seven new domains but I was beaten to it by a Mikko Hypponen (a very well known security bod). You can read his tweet with the details here. However it wasn’t all bad as I did turn up one new domain:
tusexpo2015[.]com
This seems likely to be designed to fool attendees of this conference. Given the fact these domains are now all blown it seems unlikely to be used, but it reminds us to be extremely cautious about clicking on links. This domain would likely have been used to target attendees (or potential attendees) of this conference.
What should I do next?
If you think you’ve been targeted by any the group mentioned above, then get in touch. We can advise on appropriate security measures to take, and as you will have realised I hope, will do so without acronyms or over complications.
Otherwise hopefully this has been useful in demonstrating how you can get extra usable information (or intelligence) from the reports and analysis that you receive every day. Also you can do this with the phishing emails that land in your mailbox – if it contains a link, look up the registration details and see what else you can find. You might be able to prevent future compromises.
As always thanks for reading. Any questions please ask – find us on twitter, or use the contact form.
The Cyber Security Expert