Open Source Intelligence – what is it, and how can you use it to defend your organisation?
In todays post we’re going to delve into the world of open source intelligence, and see how you can use this to defend your organisation.
So what is open source intelligence?
Without wanting to delve too deeply into what is and what isn’t ‘intelligence’, open source intelligence (OSINT) is the art of using publicly available information and tools to find out useful facts about a target, be that an individual or an organisation.
There are too many potential sources and information types to list exhaustively, however to give an idea of the variety you might use:
- Traditional Media – TV, radio, newspapers etc.
- Public data – government reports, census data, corporate governance etc.
- The Internet – social networks, wiki’s, blogs, video sharing
This blog post focuses on tools and platforms that leverage information from the Internet.
Why should I care about this?
The first thing any capable threat actors will do when they decide they want to steal information from your company, is to find out everything they can about the organisation and the people who work there. Given at this point they haven’t hacked you, or recruited your cleaners to photocopy sensitive documents (this happens), they are limited to using information in the public domain, or OSINT. Hence it is worth you putting yourselves in their shoes from time to time and seeing what sort of information it is possible to find about your organisation.
OSINT research and information gathering can give you an overall view of what information is available publicly about you or your company. Corporate self-analysis like this can yield surprising technical and non technical information and have many uses, including:
- monitoring your brand and reputation online
- searching for IP addresses and registrant details
- finding services hosted with your company name or on company servers
- checking files and documents on the web for potentially sensitive information
You might also conduct similar searches yourself when doing competitor analysis, due diligence and even staff background checks (social media analysis, as you might expect, can be very revealing).
So show me the good stuff!
There are many tools available, and many data sources. Some platforms or tools are focused on emails and domains whilst others on social media accounts, so the tool you use will depend on what it is you are trying to achieve. When researching your own organisation it is worth checking as many sources as possible.
The following are tools we like, and use frequently:
Shodan
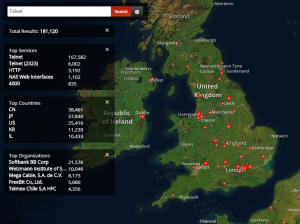
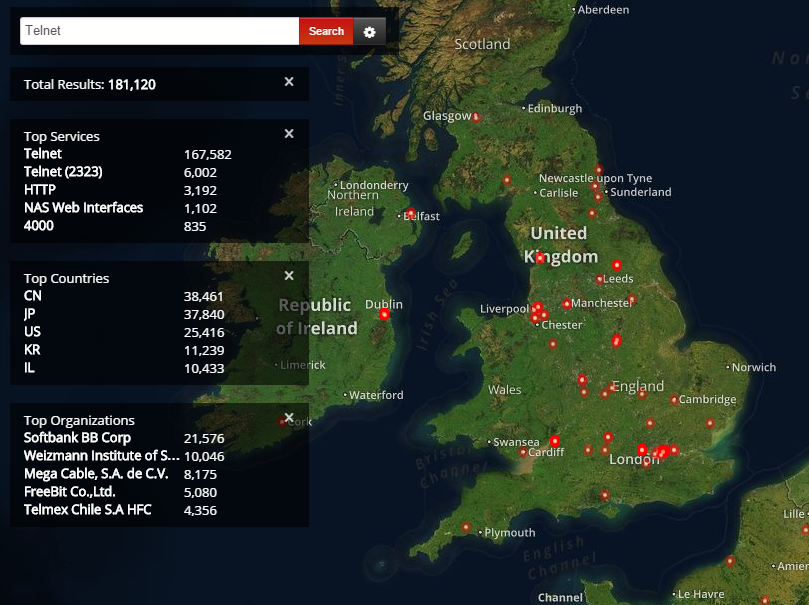
Shodan is a search engine designed for finding specific kinds of Internet connected devices. It roams the internet, attempting to connect to the devices it finds. When you connect to a device, be it by telnet, http (hyper text protocol, which underpins the web), or using any other protocol, the remote device sends you some information about itself. This will usually include something about the device itself, the version of the software it’s running and any other additional information that might have been configured (such as company or organisation name). Shodan is particularly famous for finding unprotected webcams and sometimes industrial control systems (ICS). Getting familiar with Shodan, and using it to search for domain names and IP address ranges associated is a good idea, and can reveal unexpected weaknesses in your security controls.
The above image (click to embiggen) shows devices running telnet (an insecure protocol often used to administer remote devices) in the UK.
CentralOps
CentralOps is an old favourite. You can use it to investigate domains and IP addresses, finding registrant information, DNS records, and more. For example we used it here. If you want to find out who registered that spurious domain which is similar to your corporate domain, starting with CentralOps can be helpful.
DShield
https://www.dshield.org/search.html
DShield provides a platform for users of firewalls to share intrusion information. DShield is a free and open service and very useful in identifying and investigating potentially malicious IP addresses.
FOCA
https://www.elevenpaths.com/labstools/foca/index.html
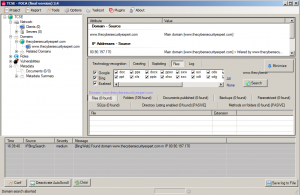
FOCA (Fingerprinting Organizations with Collected Archives) is cool. It’s a tool used mainly to find metadata and hidden information in the documents its scans. When you create a Word document, lots of information about you is also stored alongside the document content (it this additional information that is called ‘meta data’). This can include usernames, email addresses and more. Point FOCA at your website and let it run. You might be surprised how much useful information you’re revealing to hackers.
Metagoofil
http://www.edge-security.com/metagoofil.php
Similar to FOCA, though Linux based, Metagoofil is an information gathering tool designed for extracting metadata of public documents (pdf, doc, xls, ppt, docx, pptx, xlsx) belonging to a target company. Download the tool, point it at your website and see what it tells you.
Echosec
Echosec is a location based search platform on social media and other information. Browse to your office location and if anyone has been posting pictures of meeting rooms with sensitive info still readable up on the whiteboard, or what tweets from local bars might reveal to an attacker about where to hang out and find useful information about you.
This is not an exhaustive list of tools, nor a ‘how to’ on hacking an organisation. But thinking like a hacker, and seeing what information your company leaks into the public domain, can give you the edge when it comes to improving your security and protecting important assets.
Thanks for reading. Any questions, find us on twitter, or use the contact form. Also if you liked this post why not share it on Twitter or LinkedIn using the link at the top?
Jag