A different kind of incident
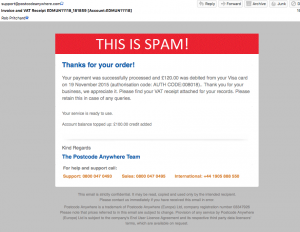
A couple of weeks ago I was reviewing my spam folder, and I saw this:
(click to embiggen).
I immediately burst out laughing, and was very impressed indeed with whoever had done this.
This is an incident
This was a pretty standard phishing email. It used the tried an tested method of pretending to be a receipt for some transaction or other in the hope that you, the victim, will open the attachment in a panic, keen to work out what has happened and to get your money back. If you open the spreadsheet attachment, and enabled macros, a nasty piece of software is downloaded to your computer that aims to steal your online banking credentials.
Now, the amount of effort crooks put into these emails varies hugely. As an example I received this missive just yesterday:
“Good morning
Please review the receipt attached to this email. The Transaction should appear on your account within 2 days.
Thanks Brody Miranda”
Not much effort spared there. It’s easier for crooks if they can just copy an existing email, and spoof the email source address. This means they can just edit the text a bit, add the malicious attachment, and hit send on their latest campaign. The original senders of the email that is copied are entirely innocent of involvement – the crooks will have got the email from the mailbox of someone they have already compromised, and who received it legitimately (which is why these spoofed emails are often clearly copied and edited marketing emails).
In this case our victim company was PCA Predict, and it was they that had the innovative idea that resulted in the ‘this is spam’ warning in the screenshot above. You can read their account of the incident here.
The crooks got hold of a copy of a real email from PCA Predict, tailored it to make it look like a receipt, added a malicious attachment, and sent it out to a huge list of victims. However, the email was html (the same language used to create webpages), meaning the images are not sent with the email itself. An html email will contain text, formatting instructions, and links to image hosted on the senders computer infrastructure. Your email browser turns this into a nice looking email, and retrieves and displays the associated images. The crooks had not changed any of these details, meaning their spam email was still pointing to an image on a server controlled by PCA Predict. PCA Predict swapped that image for the “This is Spam!” warning above, an action which I am sure saved many, many people from opening the malicious attachment. They deserve much kudos for that.
Incident planning
I do a lot of work on incident management and planning, but that is usually focussed on dealing with a compromise, or lost data. I had never thought of what happens when your company email is stolen and reused in a phishing campaign. So I reached out to PCA Predict, firstly to say awesome work, and secondly to see what had happened and how they handled it. Again, you can read their account of the incident in the link above.
The first thing that struck me was the scale of the fallout. Quoting from PCA Predict: “We had over 6,000 calls and 40,000 emails from concerned members of the public“.
Ponder those numbers for the moment, and consider those responses were only the people who got in touch. There will have been many more who either didn’t reach out to PCA Predict because they realised this was spam, those who didn’t because they just assumed it was a mistake (though they might have opened the attachment), and more again who never saw it because it wound up in a spam folder. PCA Predict estimate at least 1.5 million of these emails were sent.
This, as their blog makes clear, was a huge issue in terms of handling the volumes of calls and emails. The steps they took, changing their outgoing phone message, putting up a warning on their home page, and changing the email image to the warning, reduced that problem. Initially also they had to deal with the possibility that their infrastructure really was the source of the message, and that perhaps they had been hacked. Reviewing the message headers (the hidden information that comes with an email, but elements of which are also subject to spoofing) re-assured them they weren’t, and the fact the people calling were not actually their customers showed that their customer details had not been compromised (I got the email, and am not a customer).
For those readers that are interested, my email was sent from 182.74.238.194, which is an Indian ISP and has a poor reputation, presumably because it has been sending phishing emails. The owner of that device is probably just another innocent victim, who has had their computer compromised and taken over by criminals. The attachment is detailed here.
What can we learn from this?
Well, I’ve learnt you don’t have to be a victim of hacking to have to respond to an incident. I will be including this kind of scenario in future planning work. For PCA Predict the main and most immediate problem was how to deal with the huge numbers of people who suddenly tried to get in touch with them. They were able to respond quickly, and very smartly. If you are thinking about incident response, work through this scenario. If a fake invoice from your company landed in 1.5 million inboxes tomorrow and small percentage of those recipients got in touch believing it to be real, what would you do? I don’t have the answers to that – it will vary from company to company. But you can make your life easier by planning for it, along with other incident scenarios, in advance.
Communications are a big deal anyway for incident response. Even more so now the media are so keen on hacking stories. So always plan, and test, your communications. Do you have up-to-date contact lists? Who can talk to the media, and what should they say? What should you tell customers in the event of an incident (even if, as in this case, you are not at any fault).
There are also the practical takeaways – notably the changing of the email image to warn people the email was spam.
Having confidence in the integrity of your systems and network will also help, as you will be confident when assuring customers that you have not been breached and their details are safe. So if you are thinking of reviewing your security, or implementing new security measures, then don’t delay. And do consider your incident response procedures – how you respond to an incident is critical. It can reduce the impact to you and your customers, and there is nothing worse than trying to work out how to do all this on the fly and under pressure.
As I always tell my students when running training courses; The best way to learn is through experience. But its quicker, and often much cheaper, to learn from the experiences of others.
And yes, I do say it in a mystical way whilst staring into the middle distance. And then I make them wash my car.
So, in summary, congratulations to PCA Predict for the way they handled this incident, and also thanks to them for talking to me about it, and letting me blog about it.
Thanks for reading. Any questions, find us on twitter, or use the contact form. Also if you liked this post why not share it on Twitter or LinkedIn using the link at the top?
Rob